The average number of SaaS apps are now at 89 per organization, according to Okta, up 24% since 2016. All those apps have become one of the most critical cybersecurity challenges – and a new report underscores how vulnerable they are.
In its annual SaaS Application Security Insights (SASI) report, SaaS Alerts said it analyzed 136 million SaaS security events in 2021 and found that the most common critical SaaS alerts are geographical violations, third-party app connections, and multiple account lockouts, and guest accounts and file sharing are leading causes of unnecessary security risk.
SaaS Alerts looked at more than 2,000 SMBs for the report, and because the company’s SaaS app security and management platform is only available through the MSP channel, the data is specifically focused on SMBs who are served by managed service providers (MSPs).
Also read: Top 15 Managed Security Service Providers (MSSPs) of 2022
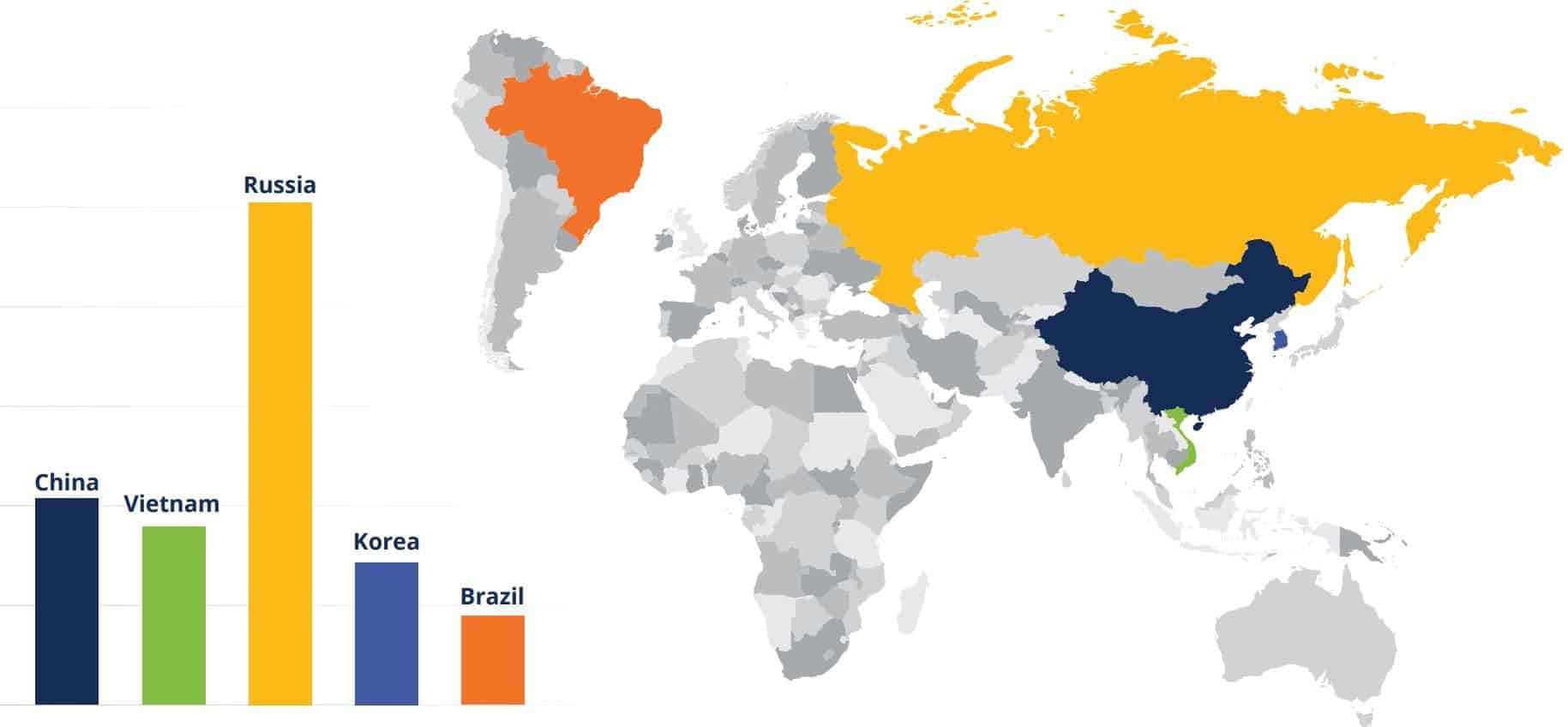
Russia and China Top Threats
The report found that most successful unauthorized logins originated from Russia, with China, Vietnam, Korea and Brazil the next biggest sources (see chart below). These attacks – using valid credentials – are hard to detect without behavioral monitoring and geographical whitelisting, the report said.
While some of those attacks may be state-sponsored, many are less sophisticated hackers who are finding it easier to acquire skills. And some governments – most notably Russia – have allowed cyber criminal groups to operate from their country in exchange for cooperation and promises not to attack the host country. Ragnar Locker, for example, terminates when it encounters a machine in former USSR countries.
Also read: Best Ransomware Backup Services
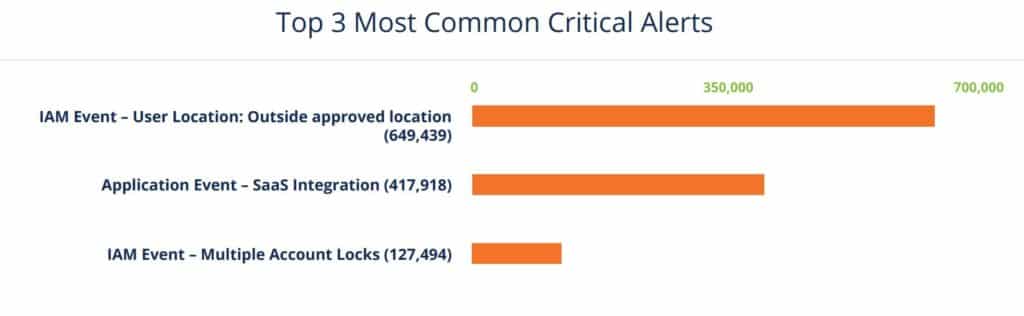
Most Common Critical Alerts
The most common critical alert, “User Location: outside approved location,” is when there’s a successful login to a user account from outside an approved location or IP address range. While those alerts are sometimes false positives due to misconfiguration of approved locations or unexpected user travel, they nonetheless indicate a significant probability that a malicious actor has succeeded in compromising an account, the report said.
The “SaaS Integration Alert” indicates that the account credentials have been used to connect to a third-party application, which may lead to data and other account information sharing between SaaS apps.
“Users often establish these connections for convenience without consideration to potential security violations,” the report noted.
“Multiple Account Lockouts” refers to accounts that are locked out four or more times in a 12-hour period. For an account to be locked means that “malicious actors have succeeded in validating a correct account name, and are actively (typically programmatically) trying password combinations to gain access to the account,” the report said.
There were about 10,000 brute force attacks against nearly 130,000 MSP user accounts monitored by SaaS Alerts.
Guest Accounts, File Sharing Are Risks
Other common vulnerabilities include guest user accounts – the report found that 42% of monitored accounts were guest accounts – and file-sharing activity.
Organizations must set up guest accounts with the minimum required access and permissions and to continuously monitor the activity of these accounts and disable unused guest accounts once they have finished their intended use, SaaS Alerts said.
Companies should also monitor SaaS file-sharing activity “to determine whether or not users are effectively and safely using document creation and file-sharing,” the report said. “End users should be trained to ensure they terminate ‘old’ share links in order to maintain proper security hygiene and mitigate risk.”
Also read: Best Incident Response Services for SMBs
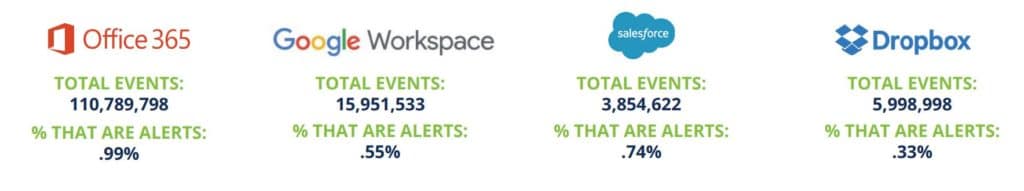
Office 365 the Most Attacked App
Not surprising given its size, Office 365 kept security pros busy, with more than 110 million events, about 1% of which triggered alerts. Google Workspace, Salesforce and Dropbox were next in terms of security activity.
‘Major Security Misconfiguration’ in ServiceNow
SaaS security provider AppOmni reported that 70% of tested instances of ServiceNow were found to be leaking data through improper customer Access Control List (ACL) configurations.
AppOmni Offensive Security Researcher Aaron Costello discovered that ServiceNow external interfaces were exposed to the public in a way that could allow a malicious actor could to extract sensitive data from records.
The issue is defined as a “misconfiguration” resulting from a combination of customer-managed ServiceNow ACL configurations and overprovisioning of permissions to guest users, AppOmni said.
‘These types of misconfigurations are common across major SaaS platforms’
“These types of misconfigurations are common across major SaaS platforms due to the complexity that inevitably comes with high levels of SaaS functionality, flexibility, and extensibility,” the company said.
“Securing SaaS is a lot more complicated than just checking a handful of settings enabling strong authentication for users,” AppOmni CEO and co-founder Brendan O’Connor said in a statement. “SaaS platforms have become business operating systems because they are so flexible and powerful. There are many valid reasons for workloads and applications running on a SaaS platform to communicate externally, such as to integrate with emails and text messages or host a support portal for your customers.
“SaaS adoption skyrocketed during the pandemic but unfortunately, investments in people, processes, and technology to secure and monitor SaaS has not kept up,” O’Connor added. “In AppOmni’s experience, significant data exposures like this are far more common than customers realize.”
Organizations have long used Role-Based Access Control (RBAC) to grant permissions for users to access resources on a SaaS platform, the company said.
“One important aspect of RBAC is the ability to allow public access to information within your ‘database,’ which could be a forum, online shop, customer support site, or knowledge base. The challenge is ensuring the right level of access when organizations update or customize SaaS applications or onboard new users.”
Read next: Top Cloud Migration Services Providers 2022