Recent Articles
-
HP Acquires Security Software Maker, Fortify Software
(Reuters) – Hewlett-Packard Co (NYSE:HPQ) said it would buy Fortify Software, a privately held security software maker based in San Mateo, California for an undisclosed sum. Fortify’s technology will allow HP to offer software that helps organizations reduce business risk, meet compliance regulations and protect against malicious application attacks. After the deal closes, HP will…
-
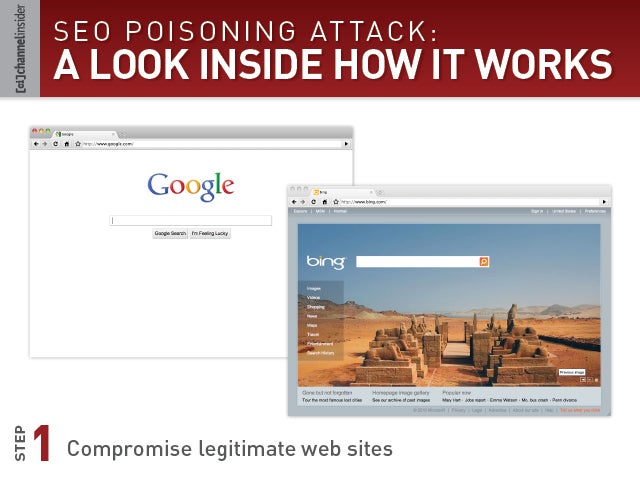
Step 1: Compromise legitimate web sites
Step 1: Compromise legitimate web sites These will be used to form the foundation of the attack. Step 2: Create SEO-friendly fake pages related to popular search topics on compromised sites In the past year hackers have taken advantage of user curiosity about the Olympics, the Haiti earthquake, Corey Haim’s death, the World Cup and…
-
SEO Poisoning Attacks 10 Ways to Protect Against Them
SEO Poisoning Attacks 10 Ways to Protect Against Them 1. Enable secure browsing functionality within the browserWhether users are fans of IE or Firefox, they need to enable secure browsing features in order to block malicious content that they may stumble upon via searching. No Title 2. Utilize free safe search and safe browsing utilitiesThere…
-
VMware’s Zimbra Appliance Offers Virtual Collaboration Solution
Virtualization specialist VMware announced the launch of the Zimbra Collaboration Suite Appliance, an e-mail and collaboration solution delivered as a virtual appliance and designed to run on the VMware vSphere platform. In addition, VMware announced that Zimbra, which it acquired in February 2010, is now fully integrated within VMware, and all Zimbra products are currently…
-
Toshiba Offers Wipe Technology for Self-Encrypting Disk Drives
Technology giant Toshiba announced Wipe for its Self-Encrypting Drive (SED) models, a technology that allows special security capabilities, such as the ability for sensitive user data to be securely erased when a system is powered down or when an SED HDD is removed from the system. The feature can also be used to erase user…
-
Same threats, different day
Same threats, different day Unified communications is a set of multi-faceted technologies that have been integrated to interoperate with one another, and so there are a lot of different security concerns relative to the type of technology and how it connects with all of the other technologies, said Jonathan Edwards, analyst for unified communications and…