Recent Articles
-
IT Security Spending What IT Executives Are Planning
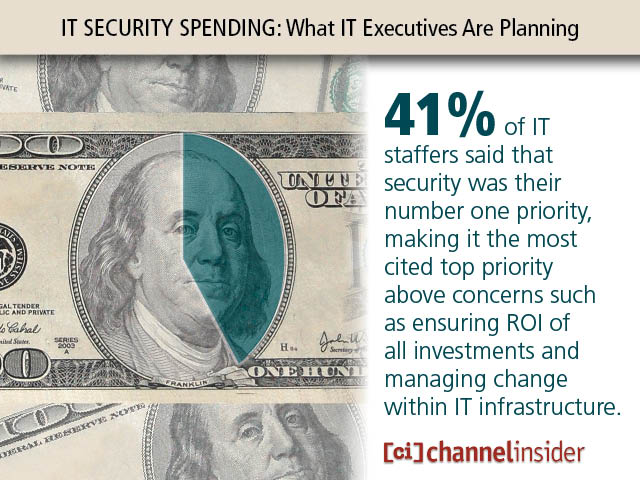
IT Security Spending What IT Executives Are Planning 41 percent of IT staffers said that security was their number one priority, making it the most cited top priority above concerns such as ensuring ROI of all investments and managing change within IT infrastructure. No Title 48 percent of organizations reported an increase in the number…
-
Apple Gets Hacked by Anonymous
In a year dominated by large-scale, high-profile security breaches, computer maker Apple has now found itself a target of hackers. The group Anonymous posted a document online that it claims contains a list of usernames and passwords for one of the company’s servers, although the group also sent out a message on Twitter saying it…
-
CA Technologies Acquires Interactive TKO for $330 Million
IT management software and solutions specialist CA Technologies announced a definitive agreement to acquire privately held Interactive TKO, a provider of service simulation solutions for developing applications in composite and cloud environments, for $330 million in an all-cash transaction. CA said the acquisition will help customers overcome the limitations of current organizational approaches, breaking down…
-
Security, Loyalty Programs to Drive Mobile Payment Adoption: Survey
U.S. consumer sentiment shows that while only two percent of adults currently use their mobile phone to pay for goods and services, 57 percent of adults expect that mobile payments will become widespread over the next three years, according to a survey released by VeriFone, a secure electronic payment solutions provider. The biggest drivers of…
-
Northrop Grumman a Regular Target of Hackers
Organized hackers have been attempting to breach aerospace and defense company Northrop Grumman for years to steal sensitive information, according to a Northrop Grumman senior executive at the Gartner security summit. The APTs (advanced persistent threats) are designed to infiltrate networks at companies and government agencies to steal intellectual property or other sensitive information. As…
-
Cloud Computing Interoperability Presents Greater Challenge to Adoption Than Security: Report
The greatest challenge facing longer-term adoption of cloud computing services is not security, but rather cloud interoperability and data portability, say cloud computing experts from IEEE, a technical professional association. At the same time, IEEE’s experts say cloud providers could reassure customers by improving the tools they offer enterprise customers to give them more control…