Firewalls used to be considered sufficient protection for an organization’s network. They are not anymore. The rapid growth of the Internet has provided hackers and other attackers with the ability to inflict major financial and public relations damage on an organization. Attackers are constantly developing new tools to exploit the applications necessary for an organization to maintain an Internet presence. As attackers develop more clever and imaginative methods to subvert or exploit the firewall, it has become apparent that advanced and layered security technologies are necessary to protect against hacker attacks.
One such technology that has gathered considerable attention from industry analysts and trade media is decoy-based intrusion protection, also known as “honeypot” technology. Honeypots, considered by many as the hottest new intrusion protection technology, are used to contain and control an attack. They are used much like deception techniques in warfare that divert enemies into attacking false troops or airfields. These systems can be applied to defend networked assets from today’s savvy attackers waging a new kind of war on the enterprise.
Honeypots were once used primarily by researchers and generally placed outside the firewall to discover hackers on a network system. Using the honeypots, researchers could study their tactics, tools, movements, and behavior. Today honeypots play an important part in enterprise security. Resellers and other distributors who understand the evolution of decoy-based intrusion protection into a critical ‘behind the firewall’ enterprise security technology will be better able to create a comprehensive intrusion protection strategy for their clients in any vertical industry. This article defines honeypots, describes their advantages, and outlines how they act as complementary components of an overall intrusion protection strategy.
What is a Honeypot?
A honeypot is a system that detects, contains and monitors unauthorized access (or other system misuse) as it happens. As a complement to network- and host-based intrusion detection systems (IDSs), honeypots act as decoy systems and divert attacks from key resources while also providing early detection of internal and external attacks.
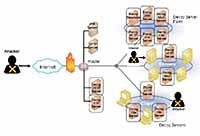
Because honeypots have no “production value,” meaning they conduct no authorized activity, any activity that takes place within a honeypot is likely the interaction of somebody or something with malicious intent. Such activity can be monitored by IT managers to gain valuable information that helps them respond to an attack more quickly, protect against future attacks and even help an organization track and prosecute attackers. Most importantly, since the honeypot is attacked, attacks to your client’s production systems are avoided.
Honeypots are described as being either low-interaction or high-interaction, a distinction based on the level of activity that the honeypot allows an attacker. A low-interaction system offers limited activity; in most cases it works by emulating services and operating systems. The main advantage of low-interaction honeypots is that they are relatively easy to deploy and maintain; they also involve minimal risk because an attacker never has access to a real operating system to cause harm.
By contrast, high-interaction honeypots involve real operating systems and real applications. Nothing is emulated. By giving attackers seemingly real systems to interact with, organizations can divert attacks away from their production systems. High-interaction honeypots make no assumptions about how an attacker will behave and provide an environment that tracks all activity. They also make it easy to apply a security policy to protect against further intrusions.
Honeypots and their Advantages
Honeypots provide multiple advantages as part of a complete security infrastructure. The first and greatest advantage of a honeypot is its intrusion detection capability. Although other intrusion detection technologies are critical, honeypots specifically provide detection of things other security solutions aren’t designed to detect, such as new types of attacks (also called “zero-day” attacks), attacks that have bypassed other defenses, attacks using encryption or tunneling, and attacks utilizing stolen credentials. For example, since a honeypot can emulate a real server it is indistinguishable from a production server to an attacker. Because a person with real credentials would not be interacting with a non-production system like a honeypot, any interaction with a decoy server using those credentials would be considered extremely suspicious. Honeypots can also detect “zero-signature attacks” –attacks that are not discernable from traffic and have no unique patterns to match.
Second, honeypots provide zero “false positives.” Many intrusion detection technologies by nature will produce a certain amount of false positives. This is because there is always a chance that valid traffic will match the characteristics the IDS uses to detect attacks. There are no false positives with a honeypot. Any communication with a honeypot is suspect simply because the device is not used for any purpose other than detecting attacks. In other words, there is no invalid traffic to produce false positives.
Third, honeypots are able to divert an attack or control the activities of an attacker. Because an IT manager has complete control over the level of activity that is allowed inside a honeypot, activities are rendered harmless because they are attacking a non-production decoy-system.
Honeypots can also detect and record incidents that may last for months. These
so-called “slow scans” are impossible to detect using conventional IDSs as the time involved makes them appear to be normal traffic.
Determining a hacked production system can be difficult since it is hard to differentiate between normal day-to-day activity and intruder activity. By capturing only unauthorized activity, honeypots can be effective as an incident response tool because they can be taken offline for analysis without affecting business operations. The newest honeypots boast stronger threat response mechanisms, including the ability to shut down systems based on attacker activity and frequency-based policies that enable security administrators to control the actions of an attacker in the honeypot.
One of the greatest advantages of honeypots is their ability to bolster network security and provide an added level of protection when combined with traditional IDSs. In contrast to the large number of alerts many IDSs can create, honeypots collect data only when someone is interacting with them, creating small data sets that make it easier and more cost-effective to identify and act on unauthorized activity.
More and more organizations are moving to encrypt all their data, either because of security issues or regulation (such as HIPAA). Not surprisingly, more and more attackers are using encryption as well, which in some cases can blind a firewall or IDS’s ability to monitor the network traffic. With a honeypot, it doesn’t matter if an attacker is using encryption; the activity will still be captured.
Conclusion
Honeypots have gained a significant place in the overall intrusion protection strategy of the enterprise. Security experts do not recommend that these systems replace existing intrusion detection security technologies; they see honeypots as complementary technology to network- and host-based intrusion protection.
The advantages that honeypots bring to intrusion protection strategies are hard to ignore. In time, as security managers understand the benefits, honeypots will become an essential ingredient in an enterprise-level security operation.
