The Cybersecurity Maturity Model Certification (CMMC) is a structured framework designed to safeguard sensitive data within the U.S. government’s defense contracts. The framework requires all defense contractors handling Controlled Unclassified Information (CUI) or Federal Contract Information (FCI) to be CMMC compliant. This article explores how CMMC works, its maturity levels, requirements, and how-to steps and explains who needs to comply.
How CMMC compliance works
CMMC compliance establishes a formal process that guides organizations within the Defense Industrial Base (DIB) to enhance their cybersecurity practices. To achieve compliance, organizations that provide goods and services to the Department of Defense (DoD) must undergo a self-assessment or one conducted by an accredited third-party assessment organization (C3PAO) to validate compliance with CUI and FCI cybersecurity processes.
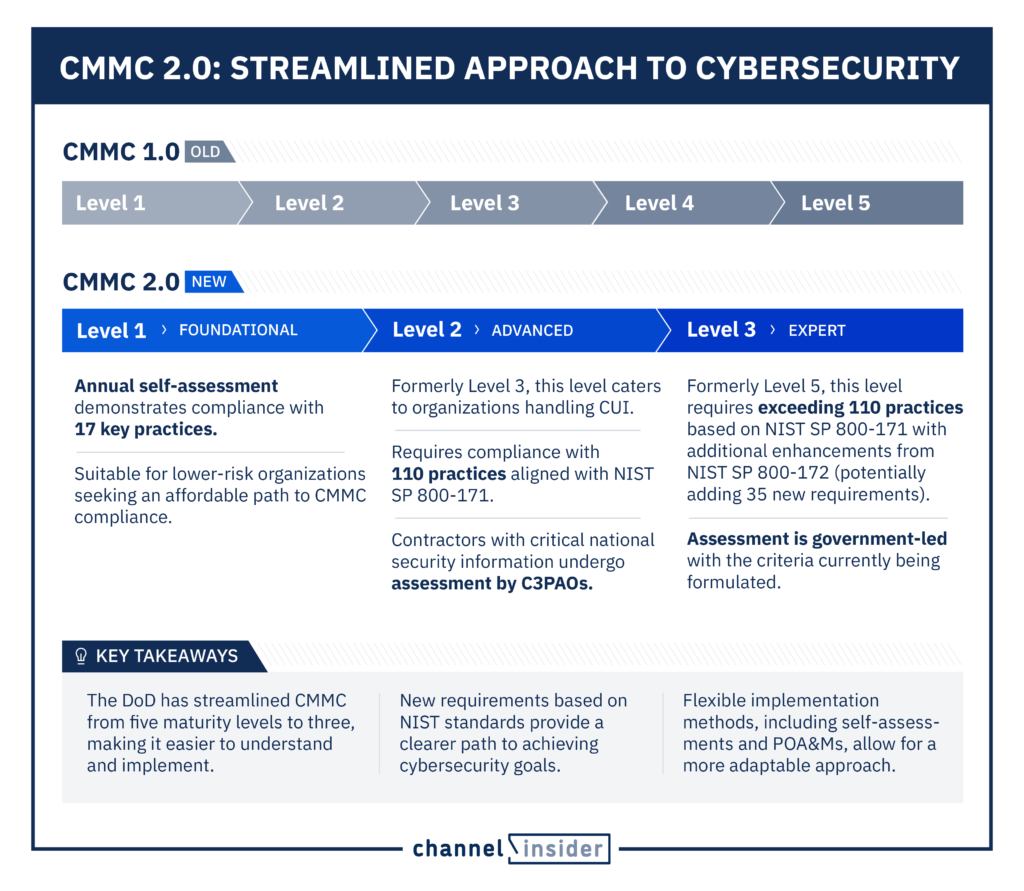
The current model, CMMC 2.0, went into effect on November 4, 2021, and consists of three maturity levels (rather than the more complex five levels of CMMC 1.0), as noted below:
- Level 1: Foundational: This level focuses on basic cybersecurity practices to protect Federal Contract Information (FCI) and requires self-assessment by the contractor.
- Level 2: Advanced: This level incorporates more comprehensive security measures to safeguard Controlled Unclassified Information (CUI) and requires assessment by a C3PAO.
- Level 3: Expert: This level requires the implementation of the most stringent cybersecurity practices to counter advanced persistent threats and protect high-value assets and requires government-led assessment with the criteria under development.
Contracting organizations need to grasp the various elements of the certification process to ensure compliance, including CMMC’s tiered security practices, assessments, integration of National Institute of Standards and Technology (NIST) and International Organization for Standardization (ISO) standards, protection methods, and widely varying costs based on contractor size and compliance level:
- Tiered practices and processes: CMMC uses a three-tiered security framework to enhance the measures DoD contractors apply to safeguard data, as noted above. This enables contractors to scale up to more rigorous standards as needed.
- Assessment levels and requirements: Level 1 contractors perform self-assessments to demonstrate adherence to foundational practices. Contractors at levels 2 and 3 require formal assessments by an accredited 3CPAO. Reassessment must take place every three years.
- Integration of standards: CMMC integrates cybersecurity standards like NIST SP 800-171 and ISO/IEC 27001 to ensure comprehensive and consistent cybersecurity practices that comply with DoD requirements.
- Protection of sensitive data: CMMC mandates measures like multi-factor authentication and data encryption. Continuous monitoring is required at Level 3 to detect and respond to threats in real time.
- Cost considerations: CMMC compliance involves significant costs that may vary from $5,000 to $2 million based on contractor size and maturity level. Contractors must budget for assessment fees, technology investments, and personnel training to maintain compliance.
Levels of CMMC compliance
Understanding the CMMC compliance framework involves navigating through its maturity levels, each designed to progressively enhance the contractor’s cybersecurity practices. The three levels each define specific requirements tailored to the sensitivity of the information DoD contractors handle:
Level 1: Foundational
Level 1 focuses on establishing basic cybersecurity practices to protect FCI. Organizations at this level must implement access control, awareness training, and basic encryption to safeguard client data. This level is suitable for contractors handling low-risk information where cybersecurity threats are minimal but still require foundational protection measures.
Level 2: Advanced
At Level 2, organizations build upon the foundational practices by implementing more robust controls, such as establishing and documenting cybersecurity practices and policies and ensuring their operational effectiveness. Level 2 is recommended for contractors dealing with moderate-risk information, where exposure to threats requires a more comprehensive approach to protection, including regular assessments.
Level 3: Expert
Level 3 represents the highest maturity level under CMMC, requiring contractors to demonstrate a comprehensive and proactive cybersecurity stance. Contractors at this level must establish, maintain, and resource a plan that ensures all cybersecurity risks are addressed. This level is suitable for contractors handling high-risk information, including CUI, where the cybersecurity threats are sophisticated and persistent.
Choosing the appropriate level of compliance depends on factors such as the sensitivity of the information handled, contractual obligations, and the client’s risk tolerance. Contractors should select a level that aligns with their operational needs. Higher levels provide more stringent measures and demonstrate a stronger commitment to protecting sensitive information, with each level building upon the previous one.
Requirements for CMMC compliance
If you’re a DIB contractor or subcontractor in the DoD supply chain, you must adhere to the CMMC requirements with the mandatory assessments determined by the maturity level you are seeking to achieve:
- Level 1 (Foundational): This level requires alignment with 17 practices derived from Federal Acquisition Regulation (FAR) 52.204-21 and a demonstration of basic cybersecurity practices to safeguard FCI based on a self-assessment.
- Level 2 (Advanced): This level requires alignment with 110 practices from NIST SP 800-171, documentation of consistent cybersecurity practices, and the ability to ensure compliance with them and additional practices.
- Level 3 (Expert): This level requires alignment with over 110 NIST SP 800-171 and other practices, establishment and maintenance of a comprehensive cybersecurity program, regular update of policies to address evolving threats, and the ability to reduce risks to CUI.
The DoD considers CMMC requirements at each of the three maturity levels a critical part of its defense against cyberthreats that continue to grow in volume and sophistication. While contractors must invest significant time, money, and discipline to adhere to these requirements, the result is attaining the required certification needed to bid on DoD contracts.
Who else outside the DIB needs to be compliant?
All organizations within the defense supply chain should become CMMC compliant, including primary contractors and subcontractors working on DoD contracts. In addition to existing defense contractors, any organization seeking to enter the defense contracting space should strive to achieve CMMC compliance at the appropriate maturity level.
Obtaining CMMC certification may not hold direct value for organizations that do not provide services or goods to the DoD. However, some organizations outside the DIB might still find indirect benefits in adopting CMMC principles, such as improving their overall cybersecurity posture, aligning with industry best practices, or enhancing readiness for future regulatory requirements in other sectors.
How to become CMMC compliant
Attaining CMMC compliance involves a series of steps and procedures designed to ensure contractors meet rigorous cybersecurity standards. Certification demonstrates adherence to these standards and opens the door to securing valuable contracts with the DoD. Several key steps are involved in becoming CMMC compliant, with numerous resources available to guide contractors through the process, as noted below.
7 steps for becoming CMMC compliant
Follow these basic steps to become CMMC compliant and obtain CMMC certification:
1. Develop and evaluate security processes: Establish a security plan and conduct a self-assessment following NIST 800-171 standards.
2. Enhance processes and report your score: Develop an action plan with specific target dates to achieve the maximum score of 110. Report this score to the DoD’s Supplier Performance Risk System (SPRS).
3. Determine your scope: Identify whether the scope is at the enterprise, organizational, unit, or program enclave level. The Cyber-AB has provided the assessment guide for CMMC 2.0 Levels 1-2.
4a. Conduct a preliminary gap analysis: Arrange an optional preliminary gap assessment with a C3PAO to pinpoint deficiencies in your security processes.
4b. Address gap analysis results: Use the feedback from the assessment organization to rectify identified security gaps and implement necessary improvements within your organization.
5. Select a C3PAO: After addressing the security gaps, use the Cyber-AB Marketplace to choose a C3PAO, such as NSF-ISR, and schedule your CMMC assessment.
6. Complete the CMMC assessment: Undergo a multi-stage assessment with your selected C3PAO and handle any necessary remediation requests.
7. Secure certification: The Cyber-AB reviews the assessment submitted by the C3PAO and makes a final certification decision. If approved, the accreditation body notifies your organization and the C3PAO, granting a three-year CMMC certification.
You can further explore the steps for becoming CMMC certified and download our 12-step compliance checklist to see what’s involved.
Tools for becoming CMMC compliant
Achieving CMMC compliance can be a complex and daunting task. Fortunately, various tools and resources are available to assist in this process. These range from assessment guides and self-assessment tools to professional consulting services and cybersecurity platforms, as listed below:
- CMMC Accreditation Body (CMMC-AB): Directories of certified assessors and organizations and training programs are available through the CMMC-AB website.
- CMMC assessment guides: You can find detailed guides for the assessment process at each CMMC level on the CMMC-AB website.
- CMMC self-assessment tools: Tools for conducting self-assessments to identify cybersecurity gaps are available through various consulting firms and cybersecurity solution providers.
- SPRSPo (Supplier Performance Risk System for the DoD): This tool for submitting self-assessment scores to the DoD is available through the DoD’s SPRSPo portal.
- Registered Provider Organizations (RPOs) and Registered Practitioners (RPs): These consultants offer preparation services for CMMC assessments and can be sourced through the CMMC-AB Marketplace.
- Vulnerability assessment tools: Tools to identify and remediate system and network vulnerabilities are provided by companies like Tenable, Qualys, Rapid7, and others.
By leveraging these and other resources, including industry groups and forums, online courses, and webinars, contractors can streamline their certification process, ensure compliance, and enhance their overall cybersecurity posture.
Frequently Asked Questions (FAQs)
Navigating the CMMC process involves understanding key aspects that impact compliance and readiness. Here are answers to common questions you may have:
- How do I determine which CMMC level my organization needs to achieve?
The required CMMC level is specified in the DoD contract you are bidding for or working on. Typically, the level is determined by the type and sensitivity of the information your organization handles. Higher levels (e.g., Level 3) require more advanced cybersecurity practices compared to lower levels (e.g., Level 1). - What is a C3PAO, and why is it important?
A C3PAO is an accredited organization authorized to conduct CMMC assessments. They play a critical role in evaluating whether your organization meets the required CMMC level. Selecting a reputable C3PAO is essential for a thorough and credible assessment process. - How long does the CMMC certification process take?
The timeline for achieving CMMC certification can vary depending on the size of your organization, the current state of your cybersecurity practices, and the level of certification required. On average, the process can take several months, including preparation, remediation, assessment, and certification. - Is CMMC certification a one-time requirement?
No, CMMC certification is not a one-time requirement. Once certified, organizations must undergo re-certification every three years to maintain their status. Additionally, maintaining compliance with the CMMC practices is an ongoing process, requiring regular reviews and updates to cybersecurity measures. - What happens if my organization fails the CMMC assessment?
If your organization fails the CMMC assessment, you will receive feedback on the deficiencies and areas that need improvement. You will have the opportunity to address these issues and request a re-assessment. The remediation period typically lasts 90 days, during which you can implement the necessary changes to achieve compliance. - Can my organization prepare for CMMC certification independently, or do we need external help?
While organizations can prepare for CMMC certification independently, many choose to seek external help from consultants or third-party assessment organizations. External experts can provide valuable guidance, conduct gap analyses, and help implement necessary cybersecurity measures to ensure a smoother certification process.
Bottom line: Ensuring robust cybersecurity and compliance
Attaining and maintaining CMMC certification is an effort that ensures defense contractors remain resilient against evolving cyberthreats. While the journey to compliance requires investment in time, resources, and expertise, the benefits of the certification are invaluable. Not only does it demonstrate a commitment to cybersecurity, but it also opens doors to new opportunities within the DIB.
By following the outlined steps, seeking assistance when needed, and continuously improving your cybersecurity practices, you can achieve sustainable compliance and contribute to the overall security of the defense supply chain.
Curious about whether to pursue NIST 800-171 or CMMC 2.0 compliance? Explore the differences between these two security standards and how the requirements for each vary.
Glossary of terms
CMMC is a complex process with many moving parts and specific terminology. We’ve included this glossary as a quick reference guide to help clarify essential terms and acronyms related to its cybersecurity maturity levels and compliance.
- Controlled Unclassified Information (CUI): Information that the U.S. government creates or possesses, or that a contractor receives or develops for the government that requires safeguarding or dissemination controls according to laws, regulations, or government-wide policies.
- CMMC Levels (1-3): The current structure of the framework (CMMC 2.0) was implemented in November 2021. While there is currently no official date for CMMC Levels 1-3 requirements going into effect, DIB contractors should begin preparing to meet these requirements well in advance of the proposed date of October 1, 2026.
- DIB (Defense Industrial Base): The network of companies and organizations that provide essential products and services to the DoD.
- CDI (Covered Defense Information): Non-classified information collected or created under a DoD contract that requires safeguarding. CDI is essentially synonymous with CUI in the context of CMMC.
- CMMC-AB (CMMC Accreditation Body): The independent organization that oversees the CMMC ecosystem, including accrediting Certified Third-Party Assessment Organizations (C3PAOs).
- CUI (Controlled Unclassified Information): Unclassified information that requires protection because disclosure could damage national security.
- FAR (Federal Acquisition Regulation): The set of rules that govern how the U.S. government buys goods and services.
- Federal Contract Information: Information provided by or generated for the government under a contract that is not intended for public release. It can include data about the contract, as well as any information generated by the contractor during the performance of a contract.
- NIST SP 800-171: A set of cybersecurity controls published by the National Institute of Standards and Technology (NIST) that are required for CMMC compliance at Levels 1-3.
- POA&M (Plan of Actions and Milestones): A document that outlines a contractor’s plan for addressing any deficiencies identified in a CMMC assessment.
