Managed detection and response (MDR) services are becoming an essential element of cybersecurity strategies for businesses and organizations. With rising threats from advanced cyberattacks, MDR services offer 24/7 monitoring, threat detection, and real-time incident response. As a result, businesses get much-needed security capabilities without the complexity of managing in-house security operations. We look at 6 of the best MDR services in the market based on determinants, such as core features, pricing, AI and automation, and customer support, among others.
Featured Partners: Email Marketing Software
What is Managed Detection and Response?
Managed detection and response (MDR) refers to outsourced security services that help businesses detect and respond to cybersecurity threats. Unlike traditional security systems that focus primarily on detection, MDR combines real-time monitoring with proactive threat-hunting and response measures. MDR solutions leverage security operations centers (SOCs), staffed by cybersecurity experts, to provide 24/7 threat detection, incident response, and ongoing risk management.
MDR is an asset for organizations that don’t have the internal resources or expertise to handle comprehensive threat detection and response operations. Managed service providers (MSPs), mid-sized enterprises, and industries with sensitive data, such as healthcare and finance, are prime candidates for MDR solutions.
MDR vs. EDR
While MDR focuses on providing comprehensive managed services, endpoint detection and response (EDR) tools focus more on endpoint-specific security. EDR tools help businesses monitor, detect, and respond to threats at the endpoint level, such as laptops, servers, or mobile devices. In contrast, MDR services go beyond detection and response at individual endpoints, integrating advanced threat intelligence and response services that encompass the entire network, including cloud and on-premise environments.
Businesses that need broader threat management and proactive incident response capabilities often benefit more from MDR services, while those with a sole focus on endpoint protection might lean toward EDR solutions. MDR typically also offers additional human expertise, such as security analysts who manage alerts and investigate threats on behalf of the business.
- SentinelOne: Best overall MDR solution
- Sophos: Best solution for advanced features
- CrowdStrike: Best for responsive customer support
- AT&T LevelBlue: Best for straightforward pricing
- TrendMicro: Best for automated and compatible MDR
- Arctic Wolf: Best for personalized threat intelligence
Top MDR services comparison
Here’s how the top service providers stack up against each other in terms of cost and top features.
| Tool | Starting Price | 24/7 Monitoring and Threat Detection | Threat Hunting | Incident Response | Managed SIEM | Endpoint Threat Detection |
|---|---|---|---|---|---|---|
| SentinelOne | $69.99/endpoint/year | ✔ | ✔ | — | ✔ | — |
| Sophos | Contact for quote | ✔ | ✔ | — | ✔ | ✔ |
| CrowdStrike | Contact for quote | ✔ | ✔ | — | ✔ | — |
| AT&T LevelBlue | $6,695/month | ✔ | — | ✔ | — | ✔ |
| TrendMicro | Contact for quote | ✔ | ✔ | ✔ | ✔ | — |
| Arctic Wolf | Contact for quote | ✔ | ✔ | — | ✔ | — |
✔=Yes —= Limited

SentinelOne
Best overall MDR solution
Overall rating: 4/5
- Cost: 3.4/5
- Core features: 3.9/5
- Customer support: 3.8/5
- Ease of use: 4.2/5
- AI and automation: 4.7/5
- Integration and compatibility: 4.4/5
SentinelOne is our pick for the best overall MDR solution due to its all-rounded approach to MDR that integrates AI-driven threat detection, threat services advisory, 24/7 monitoring, and advanced automation features. The Singularity MDR platform enables organizations to detect and respond to threats autonomously, which minimizes the need for manual interventions. Its Vigilance Respond service also offers robust incident response capabilities, with 24/7/365 MDR that promises a 30-minute mean time to respond (MTTR).
| Pros | Cons |
|---|---|
| AI-driven threat detection reduces false positives | No free trial |
| Comprehensive 24/7 monitoring | Limited support for smaller teams |
| Strong forensic capabilities for incident response | Setup can be complex for new users |
| Versatile and transparent pricing tiers to accommodate various business sizes | Limited customization in lower-tier plans |
Pricing
- Singularity Core: $69.99 per endpoint annually
- Singularity Control: $79.99 per endpoint annually
- Singularity Complete: $159.99 per endpoint annually
- Singularity Commercial: $209.99 per endpoint annually
- Singularity Enterprise: Custom pricing available
Features
- AI-powered real-time threat detection: Detect threats in real-time across endpoints and workloads with AI analytics, improving signal-to-noise ratio and reducing false positives.
- Vulnerability management: Provide comprehensive vulnerability assessments and management for both applications and operating systems.
- 24/7 monitoring: Deliver continuous monitoring and detection through SentinelOne’s global SOC network.
- Incident response automation: Automate the response process with minimal human input, enabling swift remediation of threats.
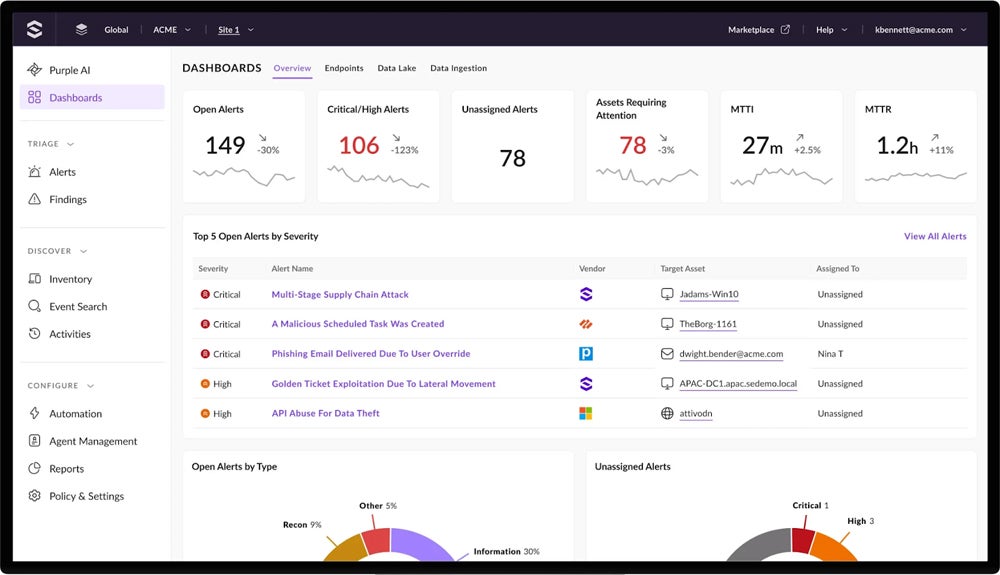
Who should use SentinelOne?
Organizations seeking an AI-powered MDR solution with automated detection and response capabilities as well as more efficient SecOps as it lessens the load and scope of security teams to help them focus on their investigation and response capabilities. It’s also well-suited for businesses that need real-time threat protection across multiple environments, including cloud and hybrid infrastructures.
Who should not use it?
Organizations that want a more focused, simpler, and more user-friendly MDR platform may find SentinelOne too advanced or complex. For a more focused and less overwhelming solution, consider a provider like Arctic Wolf.

Sophos
Best for advanced features
Overall rating: 3.8/5
- Cost: 3.3/5
- Core features: 4.2/5
- Customer support: 3.8/5
- Ease of use: 4.2/5
- AI and automation: 4.0/5
- Integration and compatibility: 3.8/5
Sophos Managed Detection and Response (MDR) stands out for its wide array of advanced features. It offers a 24/7 managed SOC with full incident response capabilities. The service includes 24/7 expert-led threat hunting, full-scale incident response, and customizable threat intelligence, which empower organizations to defend against sophisticated cyber threats in real time. The advanced capabilities, such as root cause analysis and tailored reports on security posture also help to stay ahead of rapidly evolving threats.
| Pros | Cons |
|---|---|
| Advanced threat hunting and incident response capabilities | Pricing isn’t readily listed on their pages |
| Seamless integration with existing security tools | Some smaller organizations may find it overkill |
| 24/7 SOC support with detailed reports | Initial setup can be complex for small teams |
| High ratings for customer support and threat intelligence | Admin portal can be a challenge to navigate |
Pricing
Sophos offers multiple pricing tiers but doesn’t publicly list their pricing. However, they have a proposal generator that prospective customers can use to estimate costs.
Features
- 24/7 threat detection and response: Provide continuous monitoring and immediate response actions for detected threats and lower the need for manual intervention.
- Expert-led threat hunting: Leverage a team of experts for human-led threat hunting to proactively seek out advanced cyber threats.
- Customizable service levels: Tailor the MDR service to match your organization’s specific needs, from fully outsourced to co-managed services.
- Incident response: Use full-scale capabilities to neutralize and contain threats, followed by root cause analysis and guidance for future prevention.
Who should use Sophos?
Sophos MDR is best for medium to large enterprises that need advanced managed security solutions. Companies with existing cybersecurity tools looking for a managed service to complement their in-house IT teams will benefit the most from this service. It is also well-suited for organizations with complex environments requiring high-level threat hunting and incident response.
Who should not use it?
Sophos MDR might not be ideal for smaller businesses or those looking for highly tailored solutions. While it excels in offering advanced features and real-time protection, the complexity of setup can be a challenge for smaller teams or organizations with simpler security needs. A better alternative could be Arctic Wolf, known for its more personalized threat intelligence solution.

CrowdStrike
Best for responsive customer support and ease of use
Overall rating: 3.8/5
- Cost: 2.4/5
- Core features: 3.9/5
- Customer support: 4.8/5
- Ease of use: 4.6/5
- AI and automation: 3.5/5
- Integration and compatibility: 4.2/5
CrowdStrike Falcon Complete MDR stands out for its seamless user experience and excellent customer support. This MDR tool provides a thorough solution that requires minimal hands-on management. CrowdStrike’s support options range from basic Standard Support to the highest tier, Elite Support, which offers dedicated technical account managers. These support levels are designed to ensure quick issue resolution and proactive system management for businesses of all sizes. Furthermore, Falcon’s threat intelligence has an intuitive user interface that makes it easy to navigate.
| Pros | Cons |
|---|---|
| Responsive support with multiple tiers | Opaque pricing |
| Intuitive, user-friendly interface | Falcon Complete has a number of add-ons |
| AI-powered threat detection | No free trial for Falcon Complete |
| Comprehensive technical assistance | Doesn’t have Falcon Firewall Management |
Pricing
Crowstrike doesn’t publicly list the pricing of its Complete MDR solution. Contact their sales team for pricing.
Features
- 24/7 MDR services: Provide constant monitoring with minimal manual intervention required to ensure that security issues are addressed immediately.
- Falcon Adversary Overwatch: Use proactive threat hunting to provide continuous, AI-driven threat detection and response to your users.
- Dedicated technical account manager (Elite Support): Enjoy hands-on technical guidance tailored to your business needs.
- Breach prevention warranty: Get peace of mind from Crowdstrike’s Breach Prevention Warranty provided at no extra cost.

Who should use CrowdStrike?
CrowdStrike is ideal for mid-sized to large businesses that need a reliable, easy-to-use MDR solution with responsive support options. Companies with limited internal security expertise or those that need a managed service for endpoint protection would find value in CrowdStrike’s proactive support and straightforward platform.
Who should not use it?
Businesses that want pricing information of MDR services straight away or need an MDR solution without having to consider add-ons may be better off considering alternatives. SentinelOne may be worth looking at as it presents pricing details upfront.

AT&T LevelBlue
Best for straightforward pricing
Overall rating: 3.7/5
- Cost: 3.9/5
- Core features: 4/5
- Customer support: 2.9/5
- Ease of use: 2.8/5
- AI and automation: 3.7/5
- Integration and compatibility: 4.3/5
AT&T LevelBlue makes our shortlist due to its straightforward pricing which starts at $6,695 per month. This makes it easy for organizations to estimate their security costs upfront. This pricing model is backed by the Unified Security Management (USM) platform, which offers extensive security features and is similarly transparent in its costs, listing its modules and providing organizations with both predictability and flexibility in their security investments. It also gives users the option to request a quote and customize bundles for the general USM platform, which delivers a 14-day free trial.
| Pros | Cons |
|---|---|
| Transparent pricing | Customer support has room for improvement |
| Built on the USM platform, ensuring seamless integration | Best for larger organizations |
| 24/7 expert monitoring by the SOC | Lacks out-of-the-box customizability for specific environments |
| Automation tools to streamline response workflows | Higher starting price compared to competitors |
Pricing
AT&T LevelBlue MDR starts at $6,695 per month.
Features
- 24/7 proactive monitoring: Provide continuous threat detection and incident investigation by a dedicated SOC team.
- Advanced threat intelligence: Offer up-to-date intelligence, powered by AT&T Alien Labs, to prevent emerging threats.
- Integrated security management: Enjoy security management built on the USM platform that unifies multiple security capabilities such as EDR, SIEM, and vulnerability assessment.
- Automated response: Streamline and accelerate responses to security incidents through automation and orchestration tools.
Who should use AT&T LevelBlue?
Large organizations that need transparent MDR pricing and are capable of meeting the $6,695 starting price for comprehensive security coverage across both cloud and on-premises environments.
Who should not use it?
Organizations looking for faster deployment and lower pricing may find AT&T LevelBlue’s starting price high. SentinelOne would be a better alternative for those seeking more advanced AI features with a lower overall cost of entry.

Trend Micro
Best for automated and compatible MDR
Overall rating: 3.6/5
- Cost: 1.5/5
- Core features: 4.2/5
- Customer support: 2.3/5
- Ease of use: 3.9/5
- AI and automation: 5/5
- Integration and compatibility: 5/5
Trend Micro’s XDR (Extended Detection and Response) stands out through its AI-powered threat detection and automation that delivers real-time protection across multiple endpoints. The solution also enables seamless deployment across various environments as it integrates well with existing security tools, regardless of whether in the cloud or on-premises. Trend Micro’s XDR leverages automation to reduce manual workloads, improving response times and threat-hunting capabilities. It also has an extensive roster of advanced features, qualifying it as an all-in-one MDR solution.
| Pros | Cons |
|---|---|
| Strong AI and automation capabilities | Lacks transparent pricing |
| High compatibility across environments | Customer support needs improvement |
| Advanced threat detection features | Can be complex to configure |
| Seamless integration with security tools | Can have a steep learning curve |
Pricing
Trend Micro does not provide upfront pricing for its XDR services. Potential customers must reach out to them for pricing details.
Features
- AI-driven automation: Deliver automated responses to detected threats, significantly reducing manual intervention.
- Cross-environment compatibility: Integrate effortlessly with both cloud and on-premises infrastructure for centralized security management.
- Automated data correlation: Enable a unified view of threats by correlating data across multiple threat vectors, improving overall visibility.
- Threat detection across endpoints: Provides continuous monitoring and protection for multiple endpoints, from servers to mobile devices.
Who should use Trend Micro?
Organizations with a broad range of environments and a need for robust AI-powered automation will benefit from Trend Micro’s XDR. With its seamless integration capabilities and a long list of advanced features, anyone who wants advanced threat detection tools without managing complex security stacks should consider TrendMicro.
Who should not use it?
Any business that prioritizes customer support may want to consider a different provider, as Trend Micro’s support isn’t as highly rated as some of its alternatives. CrowdStrike is a great alternative as an MDR solution with highly responsive customer support.

Arctic Wolf
Best for personalized threat intelligence
Overall rating: 3.6/5
- Cost: 2.9/5
- Core features: 4/5
- Customer support: 3/5
- Ease of use: 3.8/5
- AI and automation: 3.7/5
- Integration and compatibility: 4.2/5
Arctic Wolf is an MDR service with a heavy emphasis on personalized threat intelligence. This makes it quite attractive to organizations in the market for tailored security solutions. The service includes a variety of engineers like deployment, triage, and incident engineers, but the standout is its Concierge Security Team made up of concierge service engineers that provide hands-on support and continuous security improvement recommendations. This team works closely with clients to reduce false positives, enhance detection efficiency, and streamline incident response.
| Pros | Cons |
|---|---|
| Dedicated Concierge Security Team | No upfront pricing |
| Strong focus on personalized threat intelligence | Limited transparency on pricing tiers |
| Continuous monitoring and threat-hunting | Lacks some integration options found in other MDRs |
| Proactive threat hunting and response recommendations | May require additional in-house resources for complex deployments |
Pricing
Contact Arctic Wolf for pricing information as they don’t share it upfront.
Features
- Personalized engagement: Offer your users regular reviews of their security posture with guidance tailored to their environments.
- Log retention and search: Automate log management, enabling efficient searches and additional investigations as needed.
- Guided remediation: Collaborate with Arctic Wolf on validation of threat neutralization and ensure threats haven’t returned through collaborative detection, response, and remediation.
- Root cause analysis: Deliver deep investigations into the root causes of incidents and promote the development of customized rules and workflows.
Who should use Arctic Wolf?
Organizations that need a more hands-on approach to threat detection and response, particularly those seeking a dedicated team to help with ongoing monitoring, hunting, and personalized recommendations.
Who should not use it?
For all its personalization strengths, organizations that seek a roster of advanced features or deeper integrations may not find Arctic Wolf to be a good fit. For greater emphasis on advanced features and integrations, Trend Micro is worth considering.
How to choose MDR tools
To make the right MDR choice, here are some key factors to consider:
- Features: Look for capabilities like comprehensive threat detection, monitoring, and response capabilities, and advanced features like automated response and cyber threat hunting. Providers should also offer proactive threat-hunting services and ensure full visibility across your cloud, network, and endpoint environments.
- Integration and compatibility: It’s critical that the MDR solution integrates well with your existing security stack. If integration is a non-negotiable for you, then you want a provider that offers broad compatibility that supports diverse environments, and integrates with multiple third-party tools.
- 24/7 monitoring and response: MDR tools must offer round-the-clock monitoring and incident response. It’s vital to check how well a vendor manages 24/7 operations, including whether they have globally distributed SOCs (Security Operations Centers) or follow-the-sun support models to ensure you receive timely responses.
- Threat-hunting expertise: The quality and depth of the threat-hunting process should be a critical factor in your decision. This includes how providers leverage threat intelligence to proactively hunt for potential threats and the degree of automation involved in the threat-hunting process.
- Cost and scalability: Ensure the MDR solution offers your desired pricing model and considers your business size and type. You should also prioritize a solution that’s capable of scaling as your business grows.
Methodology
To zero in on the best MDR tools, we evaluated ten platforms across six weighted criteria, with each criterion having a maximum of five points. The service that scored the highest in each category became the criterion winner, and the solution with the best overall average was awarded the top spot.
Core features had the highest weight because the quality of the capabilities of an MDR platform determines its effectiveness in threat detection, response, and remediation. This was followed by cost considerations, as pricing transparency and flexibility are crucial factors for businesses of all sizes. Other evaluated criteria included AI and automation capabilities, customer support, and integration and compatibility, which we gave equal weights, then ease of use with the lowest weight.
- Core features (25%): We examined the platforms’ ability to deliver advanced threat detection through features like 24/7 monitoring and threat detection, incident response and containment, threat hunting, managed SIEM, and endpoint threat detection.
- Criterion winner: Multiple winners
- Cost (20%): This category considered pricing transparency, including available pricing tiers, upfront cost details, and whether the platform provides flexible pricing options.
- Criterion winner: AT&T LevelBlue
- AI and automation capabilities (20%): We assessed the use of AI for behavioral analytics, endpoint intelligence, risk scoring, and more.
- Criterion winner: TrendMicro
- Customer support (15%): The availability, quality, and responsiveness of support services such as live chat, phone support, and email were evaluated, with an emphasis on user feedback to gauge overall service experience.
- Criterion winner: CrowdStrike
- Integration and Compatibility (15%): This category focused on how well each platform integrates with third-party tools, cloud environments, existing network infrastructure, APIs, and more.
- Criterion winner: TrendMicro
- Ease of Use (10%): We reviewed each platform’s ease of setup and the availability of helpful resources like knowledge bases. Intuitive design and accessibility led to higher scores.
- Criterion winner: CrowdStrike
Bottom line: The case for MDR
It’s a fact that cyber threats continue evolving at an alarming speed and scope. As a result, MDR solutions are becoming indispensable for organizations that want a more robust security posture. If you’re considering building a security team that’s capable of dealing with current and emerging threats, it’s feasible but expect that it’ll take some time before the program is effective. In the meantime, your organization will likely still be vulnerable to threats.
You may consider endpoint detection and response (EDR) tools as they are quite popular security solutions, but organizations relying solely on EDR may find limitations in their ability to fully manage threat detection, investigation, and response. If your organization needs 24/7 monitoring or requires specialized expertise to respond to incidents quickly, MDR is the logical progression from EDR and is an immediate solution for many complex security needs.
Frequently asked questions (FAQs)
What is MDR in simple words?
MDR (Managed Detection and Response) is a service where cybersecurity professionals monitor your network and systems to find and respond to cyber threats. It works like an outsourced security team that helps you detect, investigate, and contain threats. It offers protection without the need for a full in-house security team.
What is the difference between MDR and EDR?
EDR (Endpoint Detection and Response) focuses on detecting, investigating, and responding to threats specifically on endpoints, such as computers and mobile devices. MDR (Managed Detection and Response), on the other hand, is a broader service that includes 24/7 monitoring, threat hunting, and incident response, which usually spans across networks, endpoints, and cloud environments. MDR also involves human analysts to help manage and respond to incidents, making it more comprehensive than EDR alone.
How do MDR services benefit small businesses?
MDR services provide small businesses with access to enterprise-grade security without needing to build an in-house security operations center (SOC). These services offer 24/7 monitoring, threat detection, and incident response managed by expert analysts. This helps small businesses stay protected from sophisticated cyber threats without hiring dedicated security personnel.
Can MDR services integrate with my existing security tools?
Yes, most MDR services are designed to integrate with existing security tools such as SIEM (Security Information and Event Management) platforms, firewalls, and endpoint detection systems. This allows seamless data collection and analysis and enhances the overall threat detection and response capabilities across your infrastructure.



